Lockdown Mode Prevails: New Evidence of Its Capability to Block Malicious Spyware
Citizen Lab's latest report on NSO Group's new exploit chains highlights Lockdown Mode's initial success in fending off attacks, and in certain instances, alerting users to the attempted intrusion
Ever since the introduction of Lockdown Mode with iOS 16 in 2022, security researchers have been eager to gauge its effectiveness against sophisticated spyware like Pegasus.

Citizen Lab brings encouraging news for researchers. Lockdown Mode, an extreme security measure tailored for those susceptible to targeted attacks, is demonstrating its ability to fend off such threats. Citizen Lab's recent report on NSO Group's new exploit chains offers valuable insights into the mode's success in defending against attacks and, occasionally, alerting users of attempted intrusions.
Available in iOS 16, iPadOS 16, and macOS Ventura, this stringent security mode significantly restricts device functionality to minimize the attack surface exploitable by highly targeted spyware. It modifies the performance of specific apps and features, including Messages, Web browsing, FaceTime, Apple services, Shared Albums, and device connections.
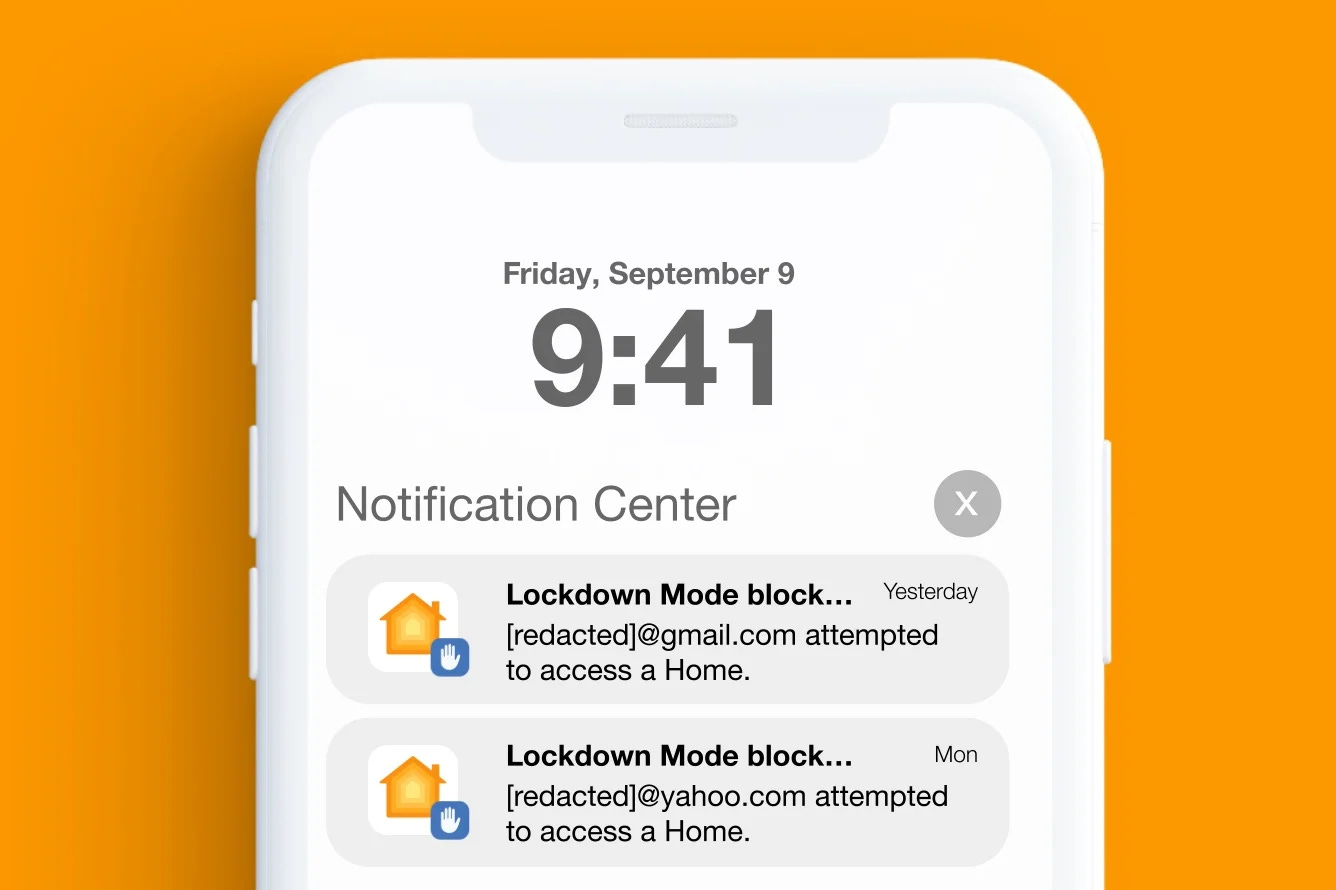
Citizen Lab's investigation into NSO Group's 2022 activities uncovered at least three iOS 15 and iOS 16 zero-click exploit chains deployed against civil society targets globally. One such exploit, dubbed "PWNYOURHOME," attacked HomeKit and iMessage through a two-step process.
The report emphasizes Lockdown Mode's capacity to counteract PWNYOURHOME. By blocking incoming invitations for Apple services like HomeKit, the mode lowers the likelihood of a successful attack. Moreover, for a brief period, users with iOS 16's Lockdown Mode activated received real-time warnings when PWNYOURHOME exploitation attempts occurred. Although there is reason to believe that PWNYOURHOME has been adjusted to prevent user notifications, the report indicates no evidence of successful infections on devices with the feature enabled.
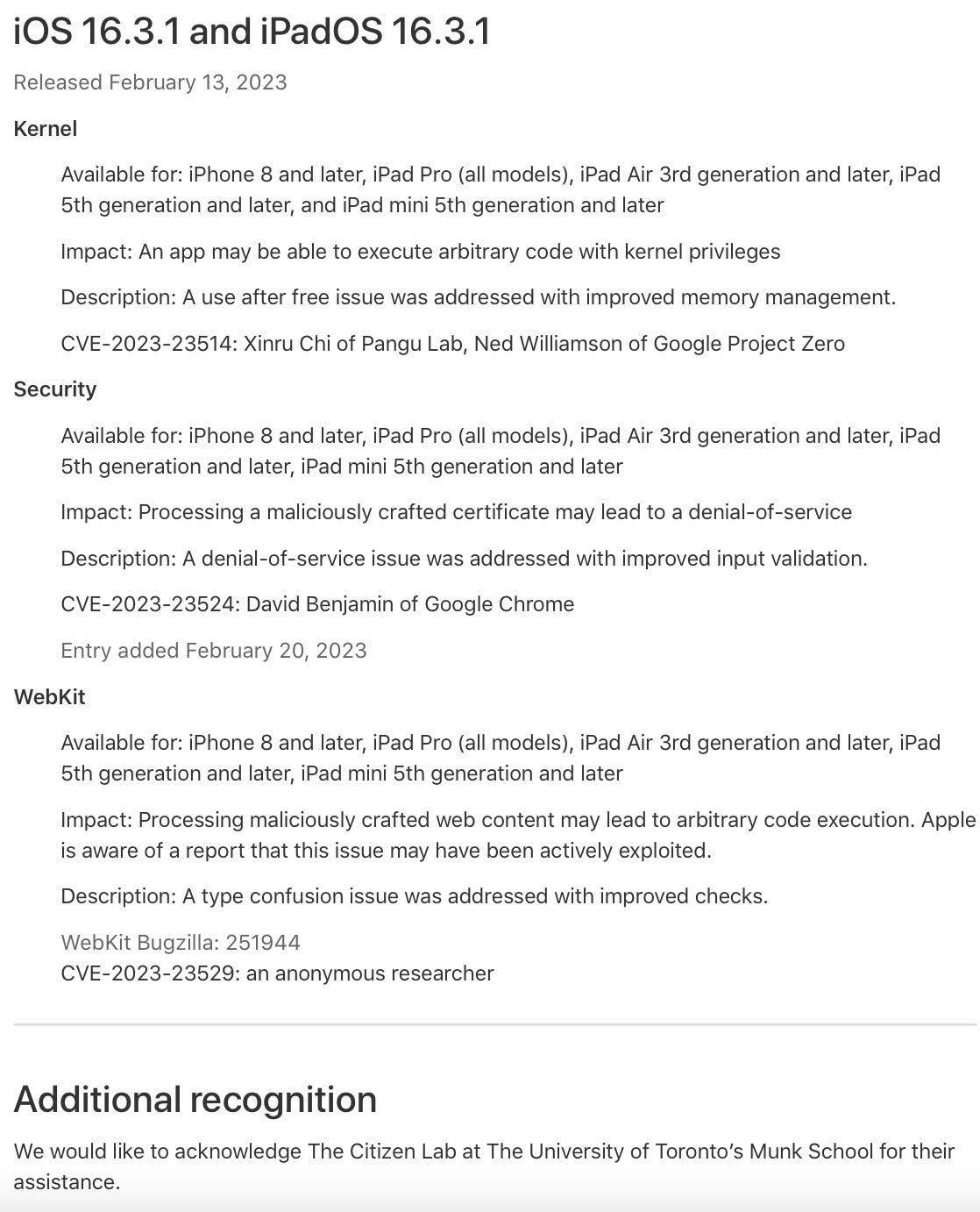
Citizen Lab states that this specific exploit was fixed in iOS 16.3.1, with Apple's security bulletin acknowledging their assistance.
It is recommended that high-risk users enable Lockdown Mode. While it may not thwart every attack, the consensus among researchers is that the mode goes a long way in mitigating attacks, with the benefits outweighing potential usability costs.
For those interested in more technical details on the exploit chains, we highly recommend reading the comprehensive report by Citizen Lab for an in-depth analysis.
References
About the security content of iOS 16.3.1 and iPadOS 16.3.1
Curious if these contain bypasses for iOS Lockdown Mode